Spookypass
Challenge Description
All the coolest ghosts in town are going to a party at a haunted house. Can you prove you deserve to enter?
Foothold
On the hackthebox platform, this challenge asks us to download a zip file. After downloading and extracting it, we get a file called pass, apparently an executable. When I ran it, it asked for a password; I certainly didn't have much success. I could even try a password-cracking script, but I don't think that's the intention, since it's not typical for a CTF of this type.
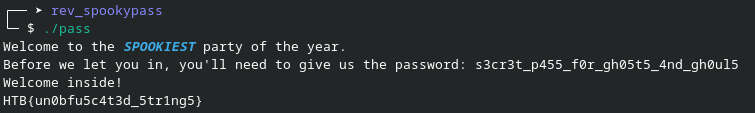
┌── ➤ rev_spookypass
└─ $ ./pass
Welcome to the SPOOKIEST party of the year.
Before we let you in, you'll need to give us the password: htb
You're not a real ghost; clear off!It came to mind to use Ghidra, a reverse engineering tool that allows us to read compiled code. Opening the file with Ghidra, I was able to easily see the code, and it contained the expected password to decrypt the executable.
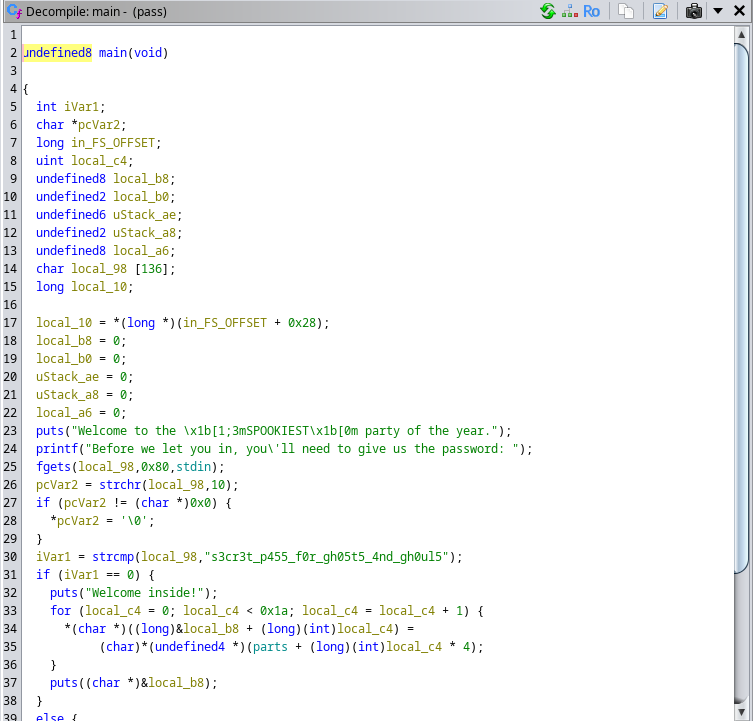
Using the password, I got the flag and the challenge solved.